I'm testing pushing out the vuln tool and it works fine reporting back vulnerability status (I'm grabbing registry keys). On newly image win7.
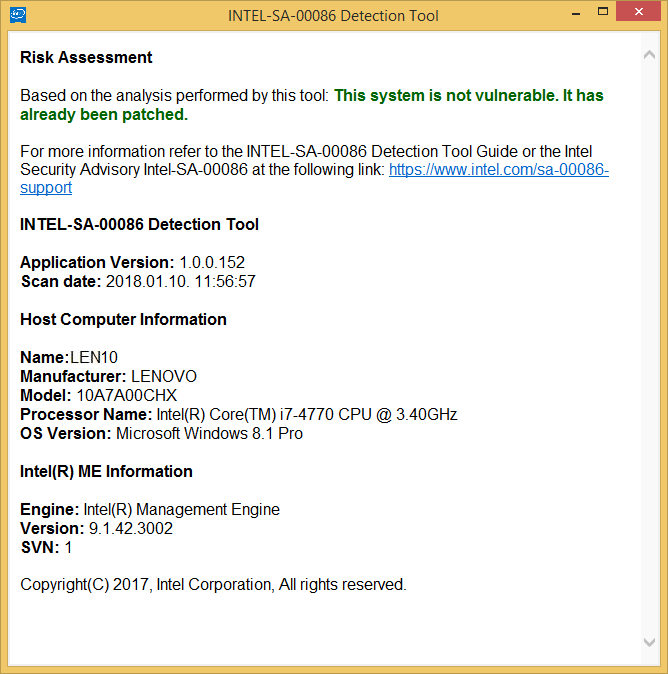
Intel® Management Engine (Intel® ME 6.x/7.x/8.x/9.x/10.x/11.x), Intel® Trusted Execution Engine (Intel® TXE 3.0), and Intel® Server Platform Services (Intel® SPS 4.0) vulnerability (Intel-SA-00086)
| Note | This article describes issues related to security vulnerabilities found in the Intel® Management Engine Firmware. This article doesn't contain information related to the processor side-channel vulnerability (known as Meltdown/Spectre). If you're looking for information on the Meltdown/Spectre issue, go to Side-Channel Analysis Facts and Intel® Products. |
In response to issues identified by external researchers, Intel has performed an in-depth comprehensive security review of the following with the objective of enhancing firmware resilience:
- Intel® Management Engine (Intel® ME)
- Intel® Trusted Execution Engine (Intel® TXE)
- Intel® Server Platform Services (SPS)
Intel has identified security vulnerabilities that could potentially impact certain PCs, servers, and IoT platforms.
Systems using Intel ME Firmware versions 6.x-11.x, servers using SPS Firmware version 4.0, and systems using TXE version 3.0 are impacted. You may find these firmware versions on certain processors from the:
- 1st, 2nd, 3rd, 4th, 5th, 6th, 7th, and 8th generation Intel® Core™ Processor Families
- Intel® Xeon® Processor E3-1200 v5 and v6 Product Family
- Intel® Xeon® Processor Scalable Family
- Intel® Xeon® W Processor
- Intel Atom® C3000 Processor Family
- Apollo Lake Intel Atom® Processor E3900 series
- Apollo Lake Intel® Pentium® Processors
- Intel® Pentium® Processor G Series
- Intel® Celeron® G, N, and J series Processors
To determine if the identified vulnerabilities impact your system, download and run the Intel-SA-00086 Detection tool using the links below.
Frequently Asked Questions Section
Available resources J tool for chevy engine repair.
- Intel official security advisory:Technical details on the vulnerability
Resources for Microsoft and Linux* users
| Note | Versions of the INTEL-SA-00086 Detection Tool earlier than 1.0.0.146 did not check for CVE-2017-5711 and CVE-2017-5712. These CVEs only affect systems with Intel® Active Management Technology (Intel® AMT) version 8.x-10.x. Users of systems with Intel AMT 8.x-10.x are encouraged to install version 1.0.0.146, or later. Installing this version helps to verify the status of their system with regard to the INTEL-SA-00086 Security Advisory. You can check the version of the INTEL-SA-00086 Detection Tool by running the tool and looking for the version information in the output window. |
Resources from system/motherboard manufacturers
| Note | Links for other system/motherboard manufacturers will be provided when available. If your manufacturer is not listed, contact them for information on the availability of the necessary software update. |
- Acer: Support Information
- ASRock: Support Information
- ASUS: Support Information
- Compulab: Support Information
- Dell Client: Support Information
- Dell Server: Support Information
- Fujitsu: Support Information
- Getac: Support Information
- GIGABYTE: Support Information
- HP Inc.: Support Information
- HPE Servers: Support Information
- Intel® NUC, Intel® Compute Stick, and Intel® Compute Card: Support Information
- Intel® Servers: Support Information
- Lenovo: Support Information
- Microsoft Surface*: Support Information
- MSI: Support Information
- NEC: Support Information
- Oracle: Support Information
- Panasonic: Support Information
- Quanta/QCT: Support Information
- Siemens: Support Information
- Supermicro: Support Information
- Toshiba: Support Information
- Vaio: Support Information
- Wiwynn: Support Information
Frequently asked questions:
JXplorer is a cross platform LDAP browser and editor. It is a standards compliant general purpose LDAP client that can be used to search, read and edit any standard LDAP directory, or any directory service with an LDAP or DSML interface. Ldap Admin Tool is a simple and easy to use LDAP Browser and LDAP administration tool designed to suit the needs of. Programs for query ″ldap admin tool mac″ Lasso Server. LDAP Admin Tool, a ldap and active directory browser and editor is a graphical tool designed to provide a user friendly environment in which to connect to any ldap aware directory server, modify data, run queries, export and print data. Microsoft Query X for Mac 10.0 is a tool utilizing Open Database Connectivity (ODBC) for importing data from databases into Microsoft Excel X. You can use Query X to create new queries or refresh existing queries that were created in. Ldap query tool for mac.
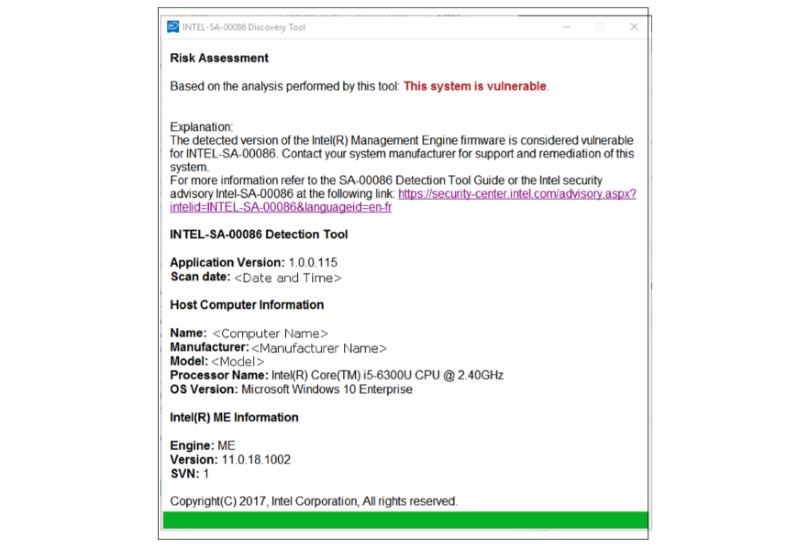
Q: The Intel-SA-00086 Detection Tool reports that my system is vulnerable. What do I do?
A: Intel has provided system and motherboard manufacturers with the necessary firmware and software updates to resolve the vulnerabilities identified in Security Advisory Intel-SA-00086.
Contact your system or motherboard manufacturer regarding their plans for making the updates available to end users.
Some manufacturers have provided Intel with a direct link for their customers to obtain additional information and available software updates (Refer to the list below).

Microsoft Gdi Detection Tool
Q: Why do I need to contact my system or motherboard manufacturer? Why can’t Intel provide the necessary update for my system?
A: Intel is unable to provide a generic update due to management engine firmware customizations performed by system and motherboard manufacturers.
Q: My system is reported as may be Vulnerable by the Intel-SA-00086 Detection Tool. What do I do?
A: A status of may be Vulnerable is usually seen when either of the following drivers aren't installed:
- Intel® Management Engine Interface (Intel® MEI) driver
- Intel® Trusted Execution Engine Interface (Intel® TXEI) driver
Q: My system or motherboard manufacturer is not shown in your list. What do I do?
A: The list below shows links from system or motherboard manufacturers who have provided Intel with information. If your manufacturer is not shown, contact them using their standard support mechanisms (website, phone, email, and so on) for assistance.
Q: What types of access would an attacker need to exploit the identified vulnerabilities?
A: If the equipment manufacturer enables Intel-recommended Flash Descriptor write protections, an attacker needs physical access to platform’s firmware flash to exploit vulnerabilities identified in:
- CVE-2017-5705
- CVE-2017-5706
- CVE-2017-5707
- CVE-2017-5708
- CVE-2017-5709
- CVE-2017-5710
- CVE-2017-5711
If the equipment manufacturer doesn't enable Intel-recommended Flash Descriptor write protections, an attacker needs Operating kernel access (logical access, Operating System Ring 0). The attacker needs this access to exploit the identified vulnerabilities by applying a malicious firmware image to the platform through a malicious platform driver.
The vulnerability identified in CVE-2017-5712 is exploitable remotely over the network in conjunction with a valid administrative Intel® Management Engine credential. The vulnerability is not exploitable if a valid administrative credential is unavailable.
If you need further assistance, contact Intel Customer Support to submit an online service request.
Purpose:
This utility is intended for re-provisioning of the platform keys AFTER applyingthe Intel (R) ME/ TXE firmware update in response to security advisory SA-00086.More information on the Intel (R) ME/ TXE update and security advisory can be found athttps://security-center.intel.com/advisory.aspx?intelid=INTEL-SA-00086&languageid=en-fr.At the link above there is also an INTEL-SA-00086 Detection Tool that assists indiscovering the platform vulnerability status described in INTEL-SA-00086.Please refer the link for a full list of affected platforms.
Prerequisites:
- Ensure Intel (R) PTT is enabled in BIOS.
- Ensure TPM CRB kernel driver is enabled on your Linux.You can check if the device exists with 'ls /dev/tpm*'
- Intel (R) MEI driver needs to be installed on the system.You can check this with 'ls /dev/mei*'
- Following dependencies need to be installed(names may vary per your Linux distribution).rpm, libcurl4-openssl-dev, libglib2.0-dev, libssl-dev, libdbus-1-dev
- Run 'build.sh' script as 'sudo' to install support packages tpm2-tss & tpm2-abrmd.
- tpm2-tss & tpm2-abrmd versions packaged here are tested with the flow.
- When installing tpm2-abrmd you can change the dbus-policy and udev-rules dir per your distribution when configuring the installation.
- If the dependency packages were installed appropriately, the build.sh should:
- Compile the Intel-SA-00086-Recovery-Utility ELF.
- Indicate the appropriate icls package versions ( i386/ x86_64 ) to install from the packages directory.
- Prior to installing the icls client libraries you can verify the rpm signaturesTo do this import the public key to verify the signature from packages/iCLS dir'rpm --import tcs-linux-pgp-public.key'To verify the package: 'rpm -K iclsClient.rpm'
- Install iCLS client libraries from the Packages folder.Instructions based on the package manager
- rpm --> 'rpm -i -nodeps iclsClient.rpm'
- alien --> 'alien -i -nodeps –-script iclsClient.rpm'
- yum --> 'yum install iclsClient.rpm'
- Please make sure system wide proxy has been setup and the platform is connected.
- After installing above dependencies a reboot is needed.
Instructions to run the Intel (R) SA-00086-Recovery-Tool For Linux* OS:
Intel-sa-00086 Detection Tool For Mac
- Please run the TPM access broker and resource manager daemon'sudo -u tss tpm2-abrmd --tcti=device &'
- Run the Intel-SA-00086-Recovery-Tool to launch the provisioning bash script.
- If you have received the necessary Intel (R) ME/ TXE firmware update then:
- You must see the message 'EPS generated by Intel (R) PTT'
- At this point the recovery application should re-provision the keys.
- After successful recovery, An NV Index for Intel (R) PTT Endorsement Key certificate is created and a copy of it is read to the file system path indicated in the Intel-SA-00086-Recovery-Tool bash script.
- OR,If you have not received the necessary Intel (R) ME/ TXE firmware update then:
- You must see the message 'EPS is generated by Manufacturer'
- At this point the platform does not trigger the recovery process.
- The recovery tool instead tries to retrieve the Intel (R) PTT Endorsement Key certificate through non recovery process.
Intel Sa 00086 Patch
NOTE: Affected platform MUST receive the Intel (R) ME/ TXE firmware update to fully mitigate the issue.