- Threat modelling works to identify, communicate, and understand threats and mitigations within the context of protecting something of value. Threat modelling can be applied to a wide range of things, including software, applications, systems, networks, distributed systems, things in the internet of.
- Students at St. Mary’s University in Canada released to open source a web-based threat modeling tool called Seasponge that they hope will provide an alternative to Microsoft’s free tool.
Microsoft Threat Modeling Tool 2016 antivirus report. This download is virus-free. This file was last analysed by Free Download Manager Lib 28 days ago.
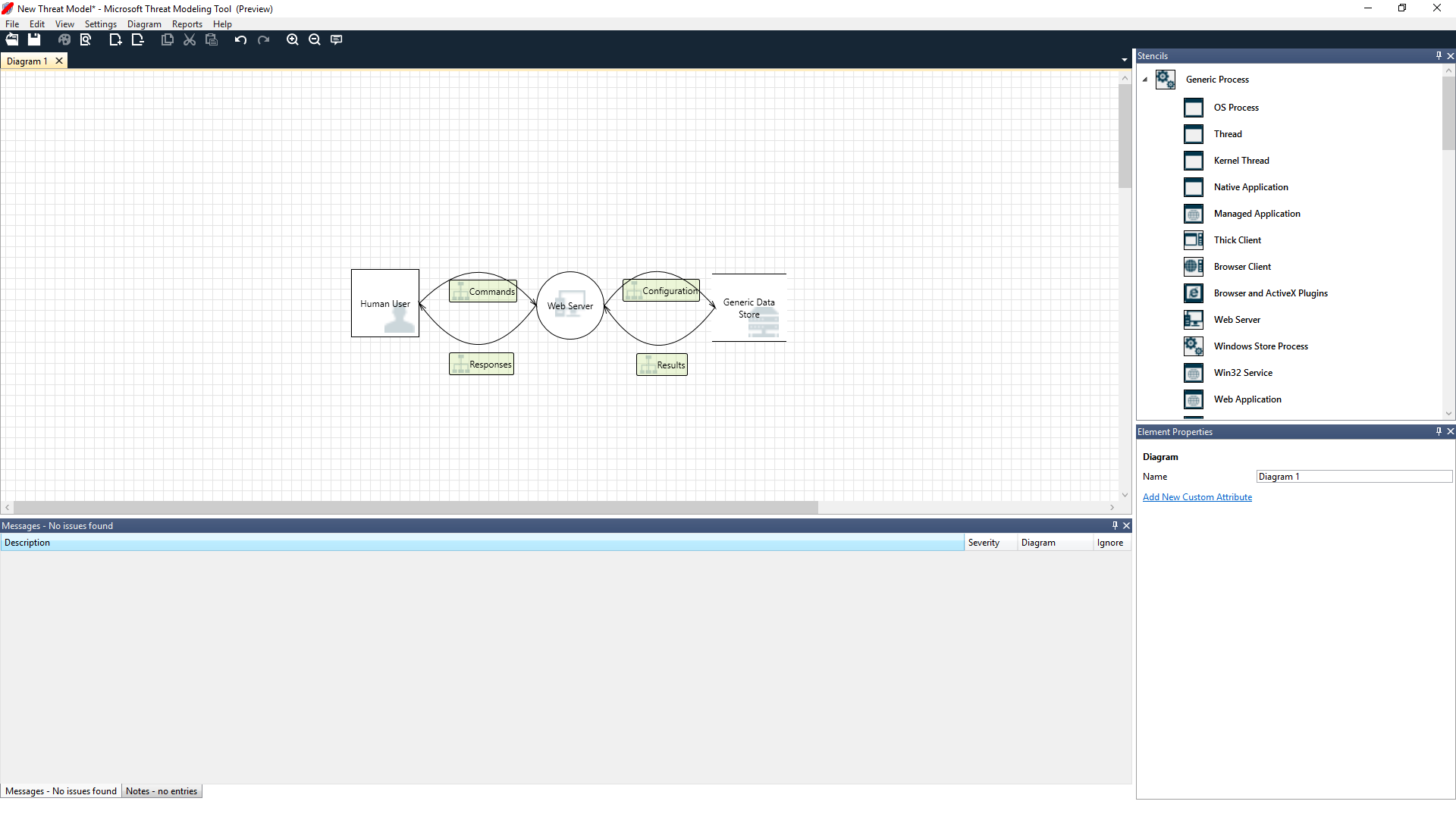
The Threat Modeling Tool is a core element of the Microsoft Security Development Lifecycle (SDL). It allows software architects to identify and mitigate potential security issues early, when they are relatively easy and cost-effective to resolve. As a result, it greatly reduces the total cost of development. Also, we designed the tool with non-security experts in mind, making threat modeling easier for all developers by providing clear guidance on creating and analyzing threat models.
However, TalkHelper call recorder, Supertintin Skype video recorder and MP3 Skype Recorder were the only ones that offers consistent accuracy of recorded data regardless of the duration of conversation and the frequency of Skype calls made. Distorted Audio Output More often than not, many Skype recorder for window just inadvertently give out a warped audio version of your calls on Skype. Mac helper tool password. This is usually cause by distortion in the digital recording of the app which is better known as spiking voice recording. In cases like this, the audio output of your recorded data will play out low or high pitched ‘chipmunk-like’ audios that one cannot make any sense of. Situations like this renders your data totally unintelligible and useless because no tangible information can be extracted from such recording.
The tool enables anyone to: Recording tool for mac.
Itool For Mac
- Communicate about the security design of their systems
- Analyze those designs for potential security issues using a proven methodology
- Suggest and manage mitigations for security issues
Here are some tooling capabilities and innovations, just to name a few:
- Automation: Guidance and feedback in drawing a model
- STRIDE per Element: Guided analysis of threats and mitigations
- Reporting: Security activities and testing in the verification phase
- Unique Methodology: Enables users to better visualize and understand threats
- Designed for Developers and Centered on Software: many approaches are centered on assets or attackers. We are centered on software. We build on activities that all software developers and architects are familiar with -- such as drawing pictures for their software architecture
- Focused on Design Analysis: The term 'threat modeling' can refer to either a requirements or a design analysis technique. Sometimes, it refers to a complex blend of the two. The Microsoft SDL approach to threat modeling is a focused design analysis technique
Microsoft Threat Modeling Tool
Next steps
Microsoft Threat Modeling Tool Tutorial
The table below contains important links to get you started with the Threat Modeling Tool:
Microsoft Threat Modeling Tool For Mac
| Step | Description |
|---|---|
| 1 | Download the Threat Modeling Tool |
| 2 | Read Our getting started guide |
| 3 | Get familiar with the features |
| 4 | Learn about generated threat categories |
| 5 | Find mitigations to generated threats |
Print Microsoft Threat Modeling Tool 2016
Resources
Microsoft Threat Modeling Tool 2014 Examples
Here are a few older articles still relevant to threat modeling today:
The best of the file-recovery apps that we reviewed make it effortless to recover files from traditional spinning hard drives, flash drives, SD cards, and other forms of portable storage. At the end of the article, you will realize that you have got best Mac data recovery software recommendation for your external hard disk drive. File deletion and recovery from Mac external hard drive. You have to stop using the external hard disk once files/folders are. https://lglucky.netlify.app/best-data-recovery-tool-for-mac-hard-drive.html. The Stellar data Recovery and Remo Data recovery software are two most powerful software that uses latest algorithm to recover data from external hard drive on Mac. The Stellar Data Recovery Software is very effective than any other software and is compatible with Mac OS X 10.5/10.6/10.7/10.8/10.9 and performs recovery from many other external.
Check out what a few Threat Modeling Tool experts have done:
