| ||||||||||||||||
- Since Network Utility is distributed with every copy of Mac OS X it stands to reason that every copy of Mac OS X has the ability to scan a port without using a GUI tool. Enter one of the best named tools in Mac OS X, stroke.
- The tool is a web interface for the well known Nmap, which is executed with the proper parameters in order to provide speed and accuracy. The scanning is done by sending packets to each port and listening for replies. The utilized scanning technique is called 'SYN scan', which sends TCP SYN packets to each port. If a port responds with SYN-ACK, it is flagged as open and a RST is sent back.
Advanced port scanner is a small and robust tool useful for scanning ports. This free network scanner scans network devices and makes it easy to find open ports quickly. It even retrieve versions of programs running on these identified ports.
Downloading Nmap
Nmap and Zenmap (the graphical front end) are available inseveral versions and formats. Recent source releases and binarypackages are described below. Older version (and sometimes newer testreleases) are available from the dist directory(and really old ones are in dist-old).For the moresecurity-paranoid (smart) users, GPG detached signatures and SHA-1hashes for each release are available in the sigsdirectory (verification instructions). Before downloading, be sure to read the relevant sections for your platform from the Nmap Install Guide. The mostimportant changes (features, bugfixes, etc) in each Nmap version aredescribed in the Changelog. Using Nmap is covered in the Reference Guide, and don't forget to readthe other available documentation, particularly the new book Nmap Network Scanning!
Nmap users are encouraged to subscribe to the Nmap-hackersmailing list. It is a low volume (7 posts in 2015), moderated listfor the most important announcements about Nmap, Insecure.org, andrelated projects. You can join the 128,953 current subscribers (as ofSeptember 2017) by submitting your email address here:
You can also get updates from our Facebook and Twitter pages.
Nmap is distributed with source code under custom license terms similar to (and derived from) the GNUGeneral Public License, as noted in the copyright page.
Microsoft Windows binaries
Please readthe Windows section of theInstall Guide for limitations and installation instructions for theWindows version of Nmap. You can choosefrom a self-installer (includes dependencies and also the Zenmap GUI)or the much smaller command-line zip file version. We support Nmap on Windows 7 and newer, as well as Windows Server 2008 and newer. We also maintain a guide for userswho must run Nmap on earlier Windows releases.
The Nmap executable Windows installer can handle Npcapinstallation, registry performance tweaks, and decompressing theexecutables and data files into your preferred location. It also includes the Zenmap graphical frontend. Skip all thecomplexity of the Windows zip files with a self-installer:
Latest stable release self-installer: nmap-7.80-setup.exe
We have written post-install usageinstructions. Please notify usif you encounter any problems or have suggestions for theinstaller.
For those who prefer the command-line zip files (Installation Instructions; UsageInstructions), they are still available. The Zenmap graphicalinterface is not included with these, so you need to runnmap.exe from a DOS/command window. Oryou can download and install a superior command shell such as thoseincluded with the free Cygwin system.Also, you need to run the Npcapand Microsoft Visual C++ 2013 Redistributable Packageinstallers which are included in the zip file. The main advantage is that these zip files are a fraction of the size of the executable installer:
Latest stable command-line zipfile:nmap-7.80-win32.zip
Linux RPM Source and Binaries
Many popular Linux distributions (Redhat, Mandrake, Suse, etc) usethe RPM package management system forquick and easy binary package installation. We havewritten a detailed guide toinstalling our RPM packages, though these simple commands usually dothe trick:You can also download and install the RPMs yourself:
Latest stable release:
x86-64 (64-bit Linux)Nmap RPM: nmap-7.80-1.x86_64.rpm
x86-64 (64-bit Linux)Ncat RPM: ncat-7.80-1.x86_64.rpm
x86-64 (64-bit Linux)Nping RPM: nping-0.7.80-1.x86_64.rpm
Optional Zenmap GUI (all platforms): zenmap-7.80-1.noarch.rpm
Source RPM (includes Nmap, Zenmap, Ncat, and Nping): nmap-7.80-1.src.rpm
Mac OS X Binaries
Nmap binaries for Mac OS X (Intel x86) are distributed as a disk image filecontaining an installer. The installer allows installing Nmap, Zenmap,Ncat, and Ndiff. The programs have been tested on Intel computersrunning Mac OS X 10.8 and later. See theMac OS X Nmap installpage for more details. Users of PowerPC (PPC) Mac machines, which Apple ceased selling in 2006, should see this page instead for support information.
Latest stable release installer: nmap-7.80.dmg
Source Code Distribution
This is the traditional compile-it-yourself format. The Nmaptarball compiles under Linux, Mac OS X, Windows, and many UNIXplatforms (Solaris, Free/Net/OpenBSD, etc.) It includes Zenmap, theGUI frontend.
Detailed Linux/BSD/Solaris compilation instructions and options are provided here, though this usually does the trick:
Most Windows users install with our Windows executable installer, but we also provide Windows source code compilation instructions.
Most Mac OS X users install with our Mac installer, but we also provide Mac OS X source code compilation instructions.
If you are compiling Nmap anyway, you might prefer to get the very latest code from our SVN source code repository rather than downloading a tarball here.
Latest stable Nmap release tarball: nmap-7.80.tar.bz2 (or gzip compressed)
Other Operating Systems
Many other operating systems support Nmap so well that I have no needto create and distribute binary packages myself. You can choose touse the packages below, or compile the sourcedistribution, which is often newer. We have created installation pages for the following platforms:
Linux (all distributions)
Microsoft Windows
Mac OS X
FreeBSD, OpenBSD, and NetBSD
Sun Solaris
Amiga, HP-UX, and Other Platforms
Nmap Site Navigation
| Intro | Reference Guide | Book | Install Guide |
| Download | Changelog | Zenmap GUI | Docs |
| Bug Reports | OS Detection | Propaganda | Related Projects |
| In the Movies | In the News | ||
Best Network Scanning Tools (Top Network and IP Scanner) for top-notch Network Security:
The network is a vast term in the world of technology. The network is known as the backbone of the telecommunication system which is used to share data and resources using data link.
The next term that comes into the frame is Network Security. Network Security consists of a set of rules, policies, and instructions that are accepted to monitor and prevent the misuse and unauthorized manipulation of a network.
Network scanning deals with Network Security and this is an activity that identifies network vulnerabilities and the loopholes to safeguard your network from unwanted and unusual behavior that can harm your system. It can harm even your personal and confidential information.
This article will brief you about the most popular Network Scanning Tools that are available in the market along with their official links and key features for your easy understanding.
What You Will Learn:
- Top Network Scanning Tools (IP and Network Scanner)
What is Network Scanning?
Network Scanning is a process which can be defined in many ways, it identifies the active hosts (Clients and servers) on a network and their activities to attack a network. It is also being used by attackers to hack the system.
This procedure is used for system maintenance and security assessment of a network.
Bootable low level format tool. HDD Low Level Format Tool will erase data from SATA, IDE, SAS, SCSI or SSD via low level access. The utility also works with any USB and FIREWIRE external drives, as well as SD, MMC, MemoryStick and CompactFlash sticks. When an USB flash drive goes wrong in a way that you could not format or access it with your window explorer, you have to recover it with low level format tool. USB flash drive Common Causes are: 1. Fake flash drive 2. Flash drive removal without using 'safely remove hardware' 3.
In short, Network Scanning process includes:
- Identifying filtering systems between two active hosts on a network.
- Running UDP and TCP network services.
- Detect TCP Sequence Number of both the hosts.
Network Scanning also refers to Port Scanning in which the data packets are sent to a specified port number.
**********
=>> Contact us to suggest your listing
**********
Top Network Scanning Tools (IP and Network Scanner)
Review of the best Network Scanner Tools which are widely used to detect network vulnerabilities.
#1) Acunetix:
Acunetix Online includes a fully automated network scanning tool that detects and reports on over 50,000 known network vulnerabilities and misconfigurations.
It discovers open ports and running services; assesses security of routers, firewalls, switches and load balancers; tests for weak passwords, DNS zone transfer, badly configured Proxy Servers, weak SNMP community strings and TLS/SSL ciphers, among others. It integrates with Acunetix Online to provide a comprehensive perimeter network security audit on top of the Acunetix web application audit.
Network scanning tool is available for free for up to 1 year!
=> Visit Official website: Acunetix Online
******************
#2) OpenVAS:
Key Features:
- The Open Vulnerability Assessment System(OpenVAS) is a free network security scanning tool.
- Many components of OpenVAS are licensed under GNU General Public License.
- The major component of OpenVAS is the Security Scanner which runs in Linux environment only.
- It can be integrated with Open Vulnerability Assessment Language (OVAL) to write vulnerability tests.
- Scanning options provided by OpenVAS are:
- Full scan: Full network scanning.
- Web server scan: For web server and web applications scanning.
- WordPress Scan: For WordPress vulnerability and WordPress web server issues.
- Proven as a powerful network vulnerability scanning tool with an intelligent custom scan.
Official Link: OpenVAS
******************
#3) Wireshark:
Key Features:
- Wireshark is an open source tool which is known as multi-platform network protocol analyzer.
- It scans data vulnerabilities on a live network between the active client and server.
- You can view network traffic and follow the network stream.
- Wireshark runs on Windows, Linux as well on OSX.
- It shows the stream construction of TCP session and includes tshark which is a tcpdump console version (tcpdump is a packet analyzer that runs on a command line).
- The only issue with Wireshark is that it has suffered from Remote Security Exploitation.
Official Link: Wireshark
******************
#4) Nikto:
Key Features:
- It is an open source web server scanner.
- It performs rapid testing to recognize suspicious behavior on the network along with any network program that can exploit network traffic.
- Some of the best features of Nikto are:
- Full HTTP proxy support.
- Customized reporting in XML, HTML and CSV formats.
- Scanning features of Nikto are updated automatically.
- It checks for HTTP servers, web server options and server configurations.
Official Link: Nikto
******************
#5) Angry IP Scanner:
Key Features:
- It is a free and open source network scanning utility with the ability to scan IP address and also performs port scan effectively and rapidly.
- The scan report consists of information such as hostname, NetBIOS (Network Basic Input/Output System), MAC address, computer name, workgroup information etc.
- Report generation is in CSV, Txt and/or XML format.
- It is based on Multi-threaded Scanning approach which is a separate scanning thread for each individual IP address, helps to improve the scanning process.
Official Link: Angry IP Scanner
******************
#6) Advanced IP Scanner:
Key Features:
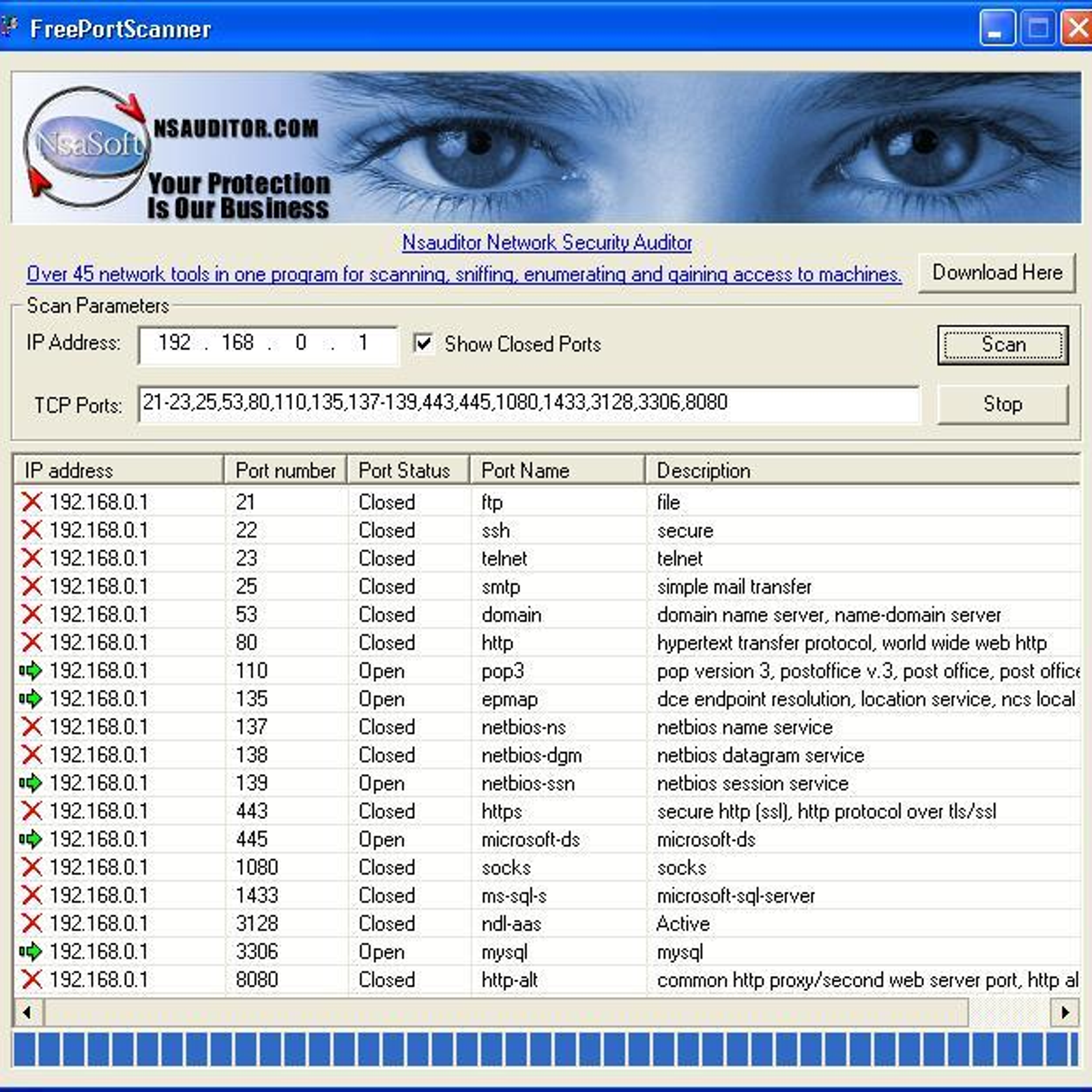
- It is a free and open source network scanning tool that works in Windows environment.
- It can detect and scan any device on a network including wireless devices.
- It allows services Viz. HTTPS, RDP etc. and FTP services on the remote machine.
- It performs multiple activities such as remote access, remote wake-on-LAN and quick shut down.
Official Link: Advanced IP Scanner
******************
#7) Qualys Freescan:
Key Features:
- Qualys Freescan is a free and open source network scanning tool that provide scans for URLs, Internet IPs and local servers to detect security loopholes.
- There are 3 types being supported by Qualys Freescan:
- Vulnerability checks: For malware and SSL related issues.
- OWASP: Web applications security checks.
- SCAP checks: Checks computer network configuration against Security Contents i.e.; SCAP.
- Qualys Freescan allows only 10 free scans. Hence, you cannot use it for regular network scan.
- Helps to detect network issues and security patches to get rid of it.
Official Link: Qualys Freescan
******************
#8) SoftPerfect Network Scanner:
Key Features:
- It is a freeware network scanning utility with advanced scanning features known as Multi-thread IPv4/IPv6 Scanning.
- Provides information such as hostname, MAC address that is connected to LAN network based on SNMP, HTTP, and NetBIOS.
- It also collects information about local and external IP address, remote wake-on-LAN and shut down.
- Helps to enhance the network performance and identifies the working state of devices on a network to check the availability a network.
- This tool is proven good for the multi-protocol environment.
Official Link: SoftPerfect Network Scanner
******************
#9) Retina Network Security Scanner:
Key Features:
- Beyond Trust’s Retina Network Security Scanner is a vulnerability scanner and solution that also provides security patch for Microsoft, Adobe, and Firefox applications.
- It is a standalone network vulnerability scanner that supports risk assessment based on optimal network performance, Operating System, and applications.
- It is a free tool which requires Windows server that provides security patches free up to 256 IPs.
- This tool performs scanning as per the credentials provided by the user and also allows a user to choose the type of report delivery.
Official Link: Retina Network Security Scanner
******************
#10) Nmap:
Key Features:
- Nmap as the name suggests, it maps your network and its ports numerically hence it is also known as Port Scanning Tool.
- Nmap comes with NSE (Nmap Scripting Engine) scripts to detect network security issues and misconfiguration.
- It is a free tool that checks for host availability by examining the IP packets.
- Nmap is a complete suite that is available in GUI and CLI( Command Line Interface) version.
- It includes the following utilities:
- Zenmap with advanced GUI.
- Ndiff for computer scan results.
- NPing for Response Analysis.
Official Link: Nmap
#11) Nessus:
Key Features:
- It is a widely used network security scanner that works with UNIX system.
- The tool was formerly free and open source but now it is available as a commercial software.
- The free version of Nessus is available with limited security features.
- Major security features of Nessus includes:
- Web-based interface
- Client-Server architecture
- Remote and local security checks
- Built-in plug-ins
- Nessus today is available with 70,000+ plug-ins and services/functionalities such as malware detection, web application scanning, and system configuration check etc.
- The advance feature of Nessus is automated scanning, multi-network scanning, and asset discovery.
- Nessus is available with 3 versions which include Nessus Home, Nessus Professional, and Nessus Manager/Nessus Cloud.
Official Link: Nessus
#12) Metasploit Framework:
Key Features:
- This tool was primarily a Penetration Testing Tool but now it is being used as Network Scanning Tool that detects network exploit.
- It was an open-source tool initially but in 2009 it was acquired by Rapid7 and got introduced as a commercial tool.
- An open-source and free edition is available with limited security features known as Community Edition.
- Advance edition of Metasploit is available as Express Edition and full-featured edition as Pro Edition.
- Metasploit Framework includes Java-based GUI whereas Community Edition, express, and Pro Edition include web-based GUI.
Official Link: Metasploit Framework
#13) Snort:
Key Features:
- Snort is known as free and open-source network intrusion detection and prevention system.
- It analyses network traffic with IP address passing through it.
- Snort is able to detect worm, port scan and other network exploit through protocol analysis and content searching.
- Snort uses Modular Detection Engine and Basic Analysis along with Security Engine(BASE) to describe network traffic.
Official Link: Snort
#14) OpenSSH:
Key Features:
- SSH(Secure Shell) helps to establish secure and encrypted communication over an insecure network link between untrusted hosts.
- OpenSSH is an open-source tool dedicated to UNIX environment.
- Access internal network using a single point access through SSH.
- It is known as Premier Connectivity Tool that encrypts the network traffic and eliminates network issues like eavesdropping, untrusted connection and connection hijacking between two hosts.
- Provides SSH tunneling, server authentication, and secure network configuration.
Official Link: OpenSSH
#15) Nexpose:
Key Features:
- Nexpose is a commercial network scanning tool that is available free as its Community Edition.
- It comes with scanning capabilities of the network, operating systems, application database etc.
- Provides web-based GUI that can be installed on Windows and Linux operating systems and even on virtual machines.
- Nexpose Community Edition includes all solid features to analyze the network.
Official Link: Nexpose
#15) Fiddler:
Key Features:
- Fiddler by Telerik is popular as Web Debugging Tool that analyzes HTTP traffic.
- Fiddler scans traffic between chosen computers over a network and analyzes sent and received data packets to monitor request and response between hosts.
- Fiddler can decrypt HTTP traffic and is also being used for system performance and security testing of web applications.
- Comes with the feature to capture the HTTP traffic automatically and allows you to choose processes for which you want to capture the HTTP traffic.
Official Link: Fiddler
Few other tools
Apart from these tools, there are many other tools that are being used for scanning the network traffic.
Nero info tool for mac. Let us take a quick look at them.
#16)Xirrus Wi-Fi Inspector:
It quickly examines Wi-Fi network with all its vulnerabilities. It is a powerful tool to troubleshoot Wi-Fi issues. Helps to check integrity and performance of your Wi-Fi network
#17)GFI LanGuard:
This commercial tool is used to scan small as well as large networks. Runs on Windows, Linux and Mac OS. This tool allows analyzing your network state from any location at any time.
#18)Total Network Monitor:
This tool monitors local network with working hosts and services on it. It reports you with colors such as Green for the successful result, Red for negative and black for an incomplete process.
#19)MyLanViewer Network/IP Scanner:
It is a popular tool for network IP scanning Wake-On-LAN, remote shutdown and NetBIOS. It is a user- friendly tool that represents your network state in an easy to analyze way.
#20)Splunk:
Git can be integrated with your development environment using command-line tools, several 'front-ends' or GUIs, and integrated tools in some IDEs. Refer to for a comprehensive list maintained in the official Git Wiki, including graphical user interfaces (GUIs). https://insidernin.netlify.app/best-git-ui-tool-for-mac.html. This section includes documentation to configure tools for use with Drupal.org and, where available, detailed directions for best-practice workflows using those tools.
It is a data collection and analysis utility that collects and analyzes data such as TCP/UDP traffic, services and event logs on a network to notify you when your network catches up with some issues.
Snipping tool for mac 2018 update. But it comes with another screenshot-taking tool, called Grab, and you can think of it as Snipping Tool for Mac. Snipping Tool for Mac: Grab. Grab is a Mac Snipping Tool alternative that makes it possible to take screenshots of your screen and save them as image files. Just like Snipping Tool for Windows, Grab has several screen-capture modes, and it also supports keyboard shortcuts.
#21)NetXMS:
The open -source tool works in a multi-platform environment and its major feature is that it supports multiple operating systems, databases and performs analysis on a distributed network.
It provides a web-based interface along with the management console and is known as Network Management and Monitoring System.
#22)NetworkMiner:
NetworkMiner is Network Forensic Analysis Tool (NFAT) for Windows, Linux and Mac OS. Gathers information about live ports, hostname, and works as Packet Capture Tool or Passive Network Sniffer.
The tool helps to perform Advance Network Traffic Analysis (NTA).
#23)Icinga2:
This is a Linux based open source network monitoring tool which is used to examine network availability and notify the users about network issues. Icinga2 provides business intelligence for in-depth and detailed analysis of the network.
#24)Capsa Free:
Monitors and analyzes network traffic and help to resolve network issues. Supports 300 network protocols and provides customized report system.
#25)PRTG Network Monitor Freeware:
Monitors network ability and usage based on a protocol such as SNMP and provides a web-based interface. Possesses feature like detailed reporting, flexible alert system, and comprehensive network monitoring but the tool is limited up to 10 sensors only.
Conclusion
Network monitoring is a crucial activity to prevent any network from intrusions. Network Scanning Tools can make this task a much easier one. Rapid scanning of networks issues make us aware of the future influence of network attacks and helps us to prepare a prevention plan to avoid them.
Ip Scanner Tool For Mac
In Today's world, each and every major software industry working on online perspective makes use of Network Scanning Tools to prepare their system stand on a network without losing its performance due to network attacks, which, in turn, makes the users to trust the system.
In this article, we have reviewed the most popular and widely used network scanning tools. There may be much more apart from these. You can choose the best suitable for your system according to your network behavior to overcome network issues.
Tools will definitely help you to prevent your network from intrusions through its loopholes.
Port Scanner Tool For Mac
**********
=>> Contact us to suggest missing listing here
**********